-
Property & Casualty
Property & Casualty Overview

Property & Casualty
We offer a full range of reinsurance products and the expertise of our talented reinsurance team.
Expertise
Publication
PFAS Regulation and Development at the European Level with Focus on Germany and France
Publication
The CrowdStrike Incident – A Wake-Up Call for Insurers?
Publication
Decision-Making in the Age of Generative Artificial Intelligence
Publication
Buildings Made of Wood – A Challenge For Insurers?
Publication
Cat Bonds – A Threat to Traditional Reinsurance? -
Life & Health
Life & Health Overview

Life & Health
Gen Re’s valuable insights and risk transfer solutions help clients improve their business results. With tailor-made reinsurance programs, clients can achieve their life & health risk management objectives.
UnderwritingTraining & Education
Publication
Fasting – A Tradition Across Civilizations
Publication
When Actuaries Meet Claims Managers – Data-Driven Disability Claims Review Business School
Business School
Publication
Chronic Pain and the Role of Insurers – A Multifactorial Perspective on Causes, Therapies and Prognosis
Publication
Simplicity, Interpretability, and Effective Variable Selection with LASSO Regression Moving The Dial On Mental Health
Moving The Dial On Mental Health -
Knowledge Center
Knowledge Center Overview

Knowledge Center
Our global experts share their insights on insurance industry topics.
Trending Topics -
About Us
About Us OverviewCorporate Information

Meet Gen Re
Gen Re delivers reinsurance solutions to the Life & Health and Property & Casualty insurance industries.
- Careers Careers
WannaCry Global Cyberattack - How Is It Affecting Insurers?

June 02, 2017
Renate Kerpen
English
Deutsch
Since it began wreaking havoc on 12 May, global cyberattack WannaCry has been making the world sit up and take note. With seemingly little regard for geography, industry or user, estimates suggest over 300,000 businesses across 150 countries have been affected, including: FedEx, PetroChina, Telefonica, Renault, Deutsche Bahn, the UK National Health Service and the Russian interior ministry.
Targeting computers using the Microsoft Windows operating system, the WannaCry ransomware “cryptoworm” has been spreading across local networks and the Internet encrypting data and demanding a ransom of at least $300 in Bitcoins be paid in order for users to regain access to their files. Should victims fail to pay up within three days, the ransom sum puportedly doubles, and after seven days, the data is destroyed for good.
Map of the WannaCry cyberattack outbreak:
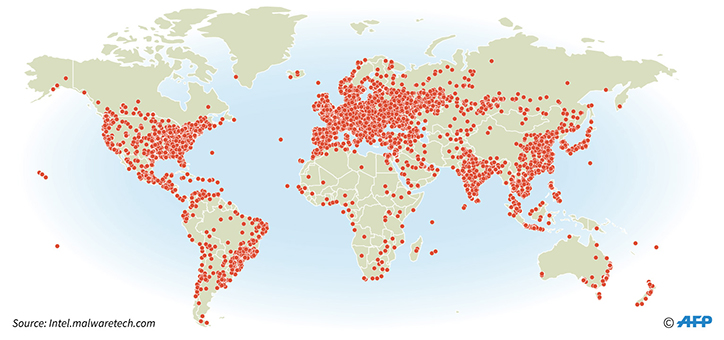
WannaCry has been affecting only older Windows versions, among them the no longer serviced but still widely used Windows XP or Windows 7. Ironically, the security gap that has been exploited was originally found and used by the NSA (U.S. National Security Agency), before the information was stolen and published by hackers. In March Microsoft distributed critical patches to close the gap but many organisations had yet to apply them.
The attack has been declared a wake-up call for companies and an increased demand for cyber insurance is predicted to follow. But what are the implications of this current attack for the insurance community?
Ransom Payments
Dissuaded by expert advice, victims have not been forthcoming with ransom payments.1 Observations of identified payment accounts suggest that the total sum amounts to less than $100,000 (although payments may be delayed due to difficulties in obtaining Bitcoins quickly).
In a number of countries, ransom payments themselves are not insurable; however, following increased demand triggered by numerous losses in 2016, expenses to mitigate the consequences of a ransomware attack are now frequently covered in cyber policies.
Business Interruption
Ransom sums often pale in comparison with other losses incurred by victims of cyber crime, not least those caused by business interruption. Estimates of BI losses inflicted at the hands of WannaCry currently stand at billions of dollars.2
However, business interruption without physical damage may not be covered by cyber insurance; when it is, coverage is often limited to specific triggers and/or sublimited in order to avoid huge and uncontrollable accumulation losses. Furthermore, a time deductible (waiting period) of at least 12 hours usually applies - a time frame in which many problems could be identified and resolved.
By locking a company’s data, it’s possible WannaCry could cause physical damage that might be covered under traditional property policies, including any consequential business interruption, though at the time of writing no such cases had been reported.
Obligations and Coverage
WannaCry’s ability to spread so successfully was only made possible by computers running older (and in some cases illegal)3 versions of Windows and companies/users not installing security patches distributed by Microsoft. Could this lapse in security be considered a failure to meet obligations of the policy? Depending on the policy, it is possible that existing insurance protection would be forfeited.
General Liability
The consequences of any negligent security may also be felt by third parties, e.g. through business interruption. Liability (as well as cyber) policies may, in certain cases, need to respond to claims made by these third parties. As with so many cyber issues, coverage comes down to the policy forms in place and how they are interpreted in the particular country or jurisdiction. Although general liability policies are often not in focus when discussing cyber coverage, they could be found to provide protection through what is being discussed with increasing fervor as “silent cover”.
D&O
The growing threat posed by cyber risk increases the potential exposure to Directors’ and Officers’ liability insurance. Losses due to alleged negligent behavior may indicate organizational failure and can lead to claims being lodged under D&O policies. A failure by management to consider and mitigate risk, including the possible use of cyber insurance, may be considered a management error and reason to sue. A publicly traded company may also have disclosure obligations that can lead to litigation if the disclosure is misleading, inadequate or fraudulent.
Conclusion
General agreement in the press indicates that, having acted responsibly and set its legal defenses well, Microsoft is beyond reproach, meaning the buck stops elsewhere.
Given that the insurance community is not immune to such attacks, we must also practice what we preach with regards to Internet security. WannaCry may be the attack currently grabbing headlines, but reports of hackers silently exploiting the same security gaps are already circulating.
Increased interest in cyber products is one expected outcome of the WannaCry attack. If you are looking for advice on how to get started in the Cyber space or how reinsurance can strengthen the portfolio you already have in place, our experts are here to help.
Endnotes
- Ransomware experts widely recommend not paying ransom. Doing so gives attackers greater means for further attacks of increasing sophistication, identifies those who pay as “weak“ (and attractive targets for return visits) and supports a criminal scheme that, if found to be lucrative with low risk of punishment, will attract numerous copycats and further demands.
- https://legalisglobal.com/insurance-coverage-for-the-wannacry-ransomware-attack/
- Pirated Windows led to WannaCry’s Spread in China and Russia, Engadget, May 2017.



