-
Property & Casualty
Property & Casualty Overview

Property & Casualty
We offer a full range of reinsurance products and the expertise of our talented reinsurance team.
Expertise
Publication
Structured Settlements – What They Are and Why They Matter
Publication
PFAS Awareness and Concern Continues to Grow. Will the Litigation it Generates Do Likewise?
Publication
“Weather” or Not to Use a Forensic Meteorologist in the Claims Process – It’s Not as Expensive as You Think
Publication
Phthalates – Why Now and Should We Be Worried?
Publication
The Hidden Costs of Convenience – The Impact of Food Delivery Apps on Auto Accidents
Publication
That’s a Robotaxi in Your Rear-View Mirror – What Does This Mean for Insurers? -
Life & Health
Life & Health Overview

Life & Health
We offer a full range of reinsurance products and the expertise of our talented reinsurance team.

Publication
Key Takeaways From Our U.S. Claims Fraud Survey
Publication
Favorite Findings – Behavioral Economics and Insurance
Publication
Individual Life Accelerated Underwriting – Highlights of 2024 U.S. Survey
Publication
Can a Low-Price Strategy be Successful in Today’s Competitive Medicare Supplement Market? U.S. Industry Events
U.S. Industry Events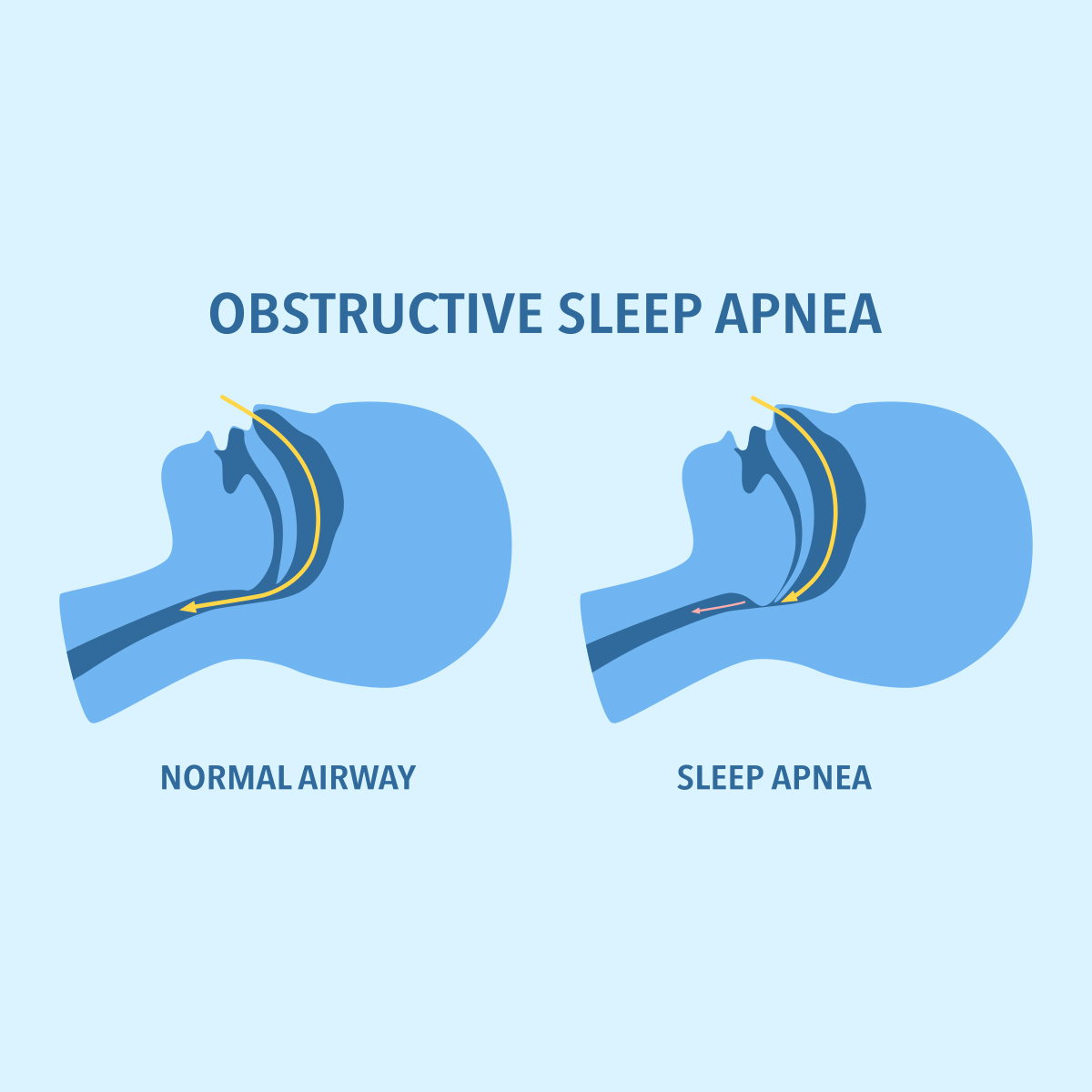
Publication
The Latest in Obstructive Sleep Apnea -
Knowledge Center
Knowledge Center Overview

Knowledge Center
Our global experts share their insights on insurance industry topics.
Trending Topics -
About Us
About Us OverviewCorporate Information

Meet Gen Re
Gen Re delivers reinsurance solutions to the Life & Health and Property & Casualty insurance industries.
- Careers Careers
The CrowdStrike Incident – A Wake-Up Call for Insurers?

February 25, 2025
Gerrit Drefke
English
Deutsch
On 19 July 2024, the U.S. cybersecurity company CrowdStrike released a faulty update for its Falcon Sensor security software, which caused massive IT outages worldwide. The update caused approximately 8.5 million Windows systems to crash, resulting in significant disruptions in various industries, particularly among airlines, banks, and hospitals.
The faulty update caused a crash of the computer systems due to a logic error. When the system restarted, a so‑called Blue Screen of Death appeared, preventing users from properly booting up the system.1 Although CrowdStrike responded quickly and provided a fix,2 many affected systems had to be repaired manually. In some cases, this extended the outage by several days. The financial damage was estimated to be at least USD 10 billion.3 The impact on U.S.‑based Delta Air Lines was particularly spectacular: The outage there resulted in the cancellation of 7,000 flights, affecting 1.3 million passengers. Delta is now claiming the resulting damage, estimated at over USD 500 million, from CrowdStrike in a court in the U.S. state of Georgia.4
Which Insurance Could Provide Coverage?
The damages claimed could be covered by CrowdStrike’s professional liability (PI/E&O) or Directors & Officers liability (D&O) insurance. Alternatively, a cyber insurance policy with third-party coverage could be triggered if CrowdStrike has taken out such a policy.
The prerequisite for such a claim is that CrowdStrike is liable for the damage incurred. This is debatable, as in the general terms and conditions CrowdStrike excludes liability for damage caused by the use of the software in critical environments that require zero fault tolerance:5
“8.6 Disclaimer. … The offerings and CrowdStrike tools are not fault-tolerant and are not designed or intended for use in any hazardous environment requiring fail-safe performance or operation. Neither of the offerings nor CrowdStrike tools are for use in the operation of aircraft navigation, nuclear facilities, communication systems, weapons systems, direct or indirect life support systems, air traffic control, or any application or installation where failure could result in death, severe physical injury, or property damage. Customer agrees that it is Customer’s responsibility to ensure safe use of an Offering and the CrowdStrike Tools in such applications and installations.”
Note the disclaimer specifies liability for use in aircraft navigation, communication systems, life-support systems, or air traffic control is excluded. Hospitals or aviation systems should therefore not rely on programs with CrowdStrike software.
In addition, it is possible that the damages were at least partially facilitated by the impacted parties themselves, which in turn would lead to shared liability. It is conceivable, for example, that a slow response by the impacted parties to the outage or outdated technology may have contributed significantly to the delays in resuming operations.6
Liability Under the EU Product Liability Directive?
The new EU Product Liability Directive (Directive 2024/2853), published in the Official Journal of the European Union on 18 November 2024,7 is too late to apply to this case. Furthermore, only natural persons are entitled to make a claim under the Directive. It should be noted that according to Art. 4 of Directive 2024/2853, software is now also to be included in the definition of a product within the meaning of the Directive and the scope of application is to cover corresponding software updates. However, according to Art. 2 (1) of Directive 20024/2853, the Directive will not apply until 9 December 2026.
Are the Damages Covered by the Injured Parties’ Insurance?
Regardless of whether CrowdStrike itself or its insurance covers the damages, it is possible that the damages could be covered by the insurance of the injured parties.
In this context, coverage by a standalone cyber insurance policy is conceivable. This would have to cover the event in question here – the faulty update of CrowdStrike. Based on the GDV model conditions for cyber insurance (AVB Cyber), it is likely that there would be no “intervention in the policyholder’s information processing system” according to A1‑2.4, 3rd Var. AVB Cyber.8 This refers to incidents of unauthorized use of IT systems, e.g., a hacker attack or even the sabotage of insured IT by employees. This also includes operating the systems incorrectly.9 However, if the damage is not caused by a person but directly by defective software, this is not considered to be interference within the meaning of the conditions. Therefore, even if an attack was assumed, the business interruption loss caused by software errors would be excluded under A4‑1.2 lit. d) AVB Cyber.10 The exclusion for “relevant security updates”, also standardized there, could apply if the “security update is specifically intended to close the security gaps of the software to which it relates and if it is “because there is a security vulnerability there or because there is objective evidence to suspect that there is a vulnerability there”.11 CrowdStrike produces a range of security software products for companies that are designed to protect computers from cyber attacks. To this end, CrowdStrike regularly distributes patches to its customers to ensure that their computers are protected against new threats. These security updates need to be checked for compatibility before installation – this is a requirement of patch management according to A1‑16.1 lit. d) AVB Cyber.12
Whether the exclusion under A4‑1.2 lit. d) AVB Cyber applies is therefore a question that will have to be decided. When answering this question, it must be considered that the GDV model conditions have only existed for about a year (February 2024).13 Insurance policies that already existed before this date may have different wording in their conditions. In particular, larger companies will have placed a high value on including losses not caused by hackers (“non-malicious acts”) – which also includes faulty security updates – in their negotiations with cyber insurers.14
In addition to traditional cyber insurance, there could be coverage through a business interruption policy. Potential cyber risks may be covered under a conventional property insurance policy that may not explicitly exclude cyber risk (so‑called silent cyber).15 However, it should be noted that since the Covid pandemic, primary insurers have specified that property damage is a prerequisite for cover, i.e., the business interruption loss is based on property damage.16 Data does not constitute property, which is why coverage under business interruption insurance is likely to be excluded.17
Conclusion
Whether damages caused by the faulty update are covered by a policy depends largely on the individual design of the contracts. For example, a cyber insurance policy that is not only aimed at attacks by hackers can also offer coverage for software errors. However, this will be the exception. Coverage under property insurance is also unlikely.
Whether the damages can be compensated by an insurance policy taken out by CrowdStrike depends essentially on the question of liability. On the one hand, CrowdStrike has taken precautions with the disclaimer described above, and on the other hand, it has a strong case for contributory negligence on the part of the software users.
What is certain is that an incident with such massive repercussions could happen at any time, including by a conventional cyber attack. Considering that in July 2024 only 1% of the systems using Microsoft were affected, the question arises as to whether and to what extent such incidents are even insurable.18
- Ronald Eikenberg, Christopher Kunz, Volker Zota, “CrowdStrike-Fiasko: Der Null Pointer ist Schuld”, heise online, 20 Jul 2024, https://www.heise.de/hintergrund/Fataler-Fehler-bei-CrowdStrike-Schuld-war-ein-Null-Pointer-9807896.html.
- “Channel File 291 Incident: Root Cause Analysis is Available”, CrowdStrike Blog, 6 Aug 2024, https://www.crowdstrike.com/en-us/blog/channel-file-291-rca-available/#:~:text=Channel%20File%20291%20Incident%3A%20Root%20Cause%20Analysis%20is%20Available&text=On%20July%2019%2C%202024%2C%20as,resulted%20in%20a%20widespread%20outage.
- Lian Kit Wee, “Here comes the wave of insurance claims for the CrowdStrike outage”, Business Insider, 22 Jul 2024, https://www.businessinsider.com/businesses-claiming-losses-crowdstrike-outage-insurance-billions-losses-cyber-policies-2024-7.
- Philipp Anz, “Delta Air Lines verklagt CrowdStrike auf Millionen Schadensersatz”, Inside IT, 28 Oct 2024, https://www.inside-it.ch/delta-air-lines-verklagt-crowdstrike-auf-millionen-schadensersatz-20241028.
- CrowdStrike Terms and Conditions, https://www.crowdstrike.com/en-us/terms-conditions/.
- Jordan Novet, Leslie Josephs, “Delta, CrowdStrike sue each other over widespread IT outage that caused thousands of cancellations”, CNBC, 25 Oct 2024, https://www.cnbc.com/2024/10/25/delta-suit-against-crowdstrike-after-it-outage-caused-cancellations.html.
- Directive (EU) 2024/2853 of the European Parliament and of the Council of 23 Oct 2024 on liability for defective products and repealing Council Directive 85/374/EEC, https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=OJ:L_202402853.
- Susanne Schier, “Nach IT‑Chaos – Warum die Versicherung vermutlich nicht zahlt”, Handelsblatt, 23 Jul 2024, https://www.handelsblatt.com/finanzen/banken-versicherungen/versicherer/crowdstrike-nach-it-chaos-warum-die-versicherung-vermutlich-nicht-zahlt/100054839.html.
- Alexander Hoffman, Botan Altundag, “Die Cyber-Versicherung: Die Basics”, CMS Blog, 6 Nov 2024, https://www.cmshs-bloggt.de/banking-finance/die-cyber-versicherung-die-basics/.
- General Insurance Conditions for Cyber Risk Insurance (“AVB Cyber”), https://www.gdv.de/resource/blob/6100/a0fed56c4947751cdc20b5206c171d98/01-allgemeine-versicherungsbedingungen-fuer-die-cyberrisiko-versicherung-avb-cyber--data.pdf. “A4.1,2 lit. d): Special exclusions: The insurance coverage excludes, without consideration of contributing causes, business interruption losses... d) resulting from the use of untested information processing systems or procedures or software not approved for the intended purpose. This exclusion does not apply to relevant security updates.”
- Lena Rudkowski, “Die AVB Cyber 2024 – Ein erster Überblick”, VersR 2024, 606 f.
- Ibid.
- “Versicherungsschutz gegen Cyberangriffe – GDV veröffentlicht neue Musterbedingungen”, 19 Feb 2024, https://www.gdv.de/gdv/medien/medieninformationen/versicherungsschutz-gegen-cyberangriffe-gdv-veroeffentlicht-neue-musterbedingungen--168132.
- Archibald Preuschat, “CrowdStrike-Opfer gehen wohl leer aus”, Frankfurter Allgemeine Zeitung, 22 Jul 2024. https://www.faz.net/aktuell/finanzen/crowdstrike-opfer-gehen-wohl-leer-aus-schaden-ist-schwer-einzuklagen-19871948.html.
- “Silent Cyber: What It Is and How You Can Cover Cyber Perils”, Marsh, 5 Dec 2019, https://www.marsh.com/en-gb/services/cyber-risk/expertise/silent-cyber-how-you-can-cover-perils.html.
- Alexander Hoffman, Botan Altundag, see endnote 9.
- OLG Brandenburg, judgment of 6 Nov 2019, Ref.: 4 U 123/19.
- “Why the CrowdStrike Incident Was Small and How Critical a Microsoft Outage Could Be”, Teamwire, 1 Aug 2024, https://teamwire.eu/en/blog/why-the-crowdstrike-incident-was-small-and-how-critical-a-microsoft-outage-could-be/.
All endnotes last accessed on 4 February 2025.





